CySCA 2014 Web Penetration Testing Write-up
Hellow Peeps !!!
Today I bring some interesting hacking challenge walkthrough. Let's see what it is,
CySCA2014 Web Penetration Testing Write-up
We need to first setup the cysca2014 box in VM. When the VM configuring we can check connectivity is their using ping commands.
Web Penetration Testing 1 – Club Status
Turn on the intercept in the burp suit and go to the web site using cysca2014 IP address. Then you can see the GET request. There are two cookies called PHPSESSID and VIP. Then we have to edit the VIP cookie value from 0 to 1 and forward the request.
Then we need to forward this packet in burp suite. Then we can get a website.
Index.php
Now we cannot access the blog.
Now we need to change VIP 0 to 1 then we can access the blog.
Now we can access Blog.
Web Penetration Testing 2 – Om nom nom nom
After completing challenge 1, you can browse on the Blog page. There is a user called Sycamore. Then go to the blog of Sycamore and there is a comment box. We can put comments on it. Then we have to find the vulnerabilities of this comment box.
Type [<script>alert(“test”)</script>](test) in the comment box and submit it. You can see the alert message.
That’s it. We found the XSS vulnerability. The next step is to steal the PHPSESSID cookie of Sycamore. To do that, we have to host a server. We can create a file name .j containing some JavaScript to steal the user cookie. We can use pythons SimpleHTTPServer to host it on port 80.
Now we can create an XSS payload for the comment field. It looks like this.
Add this comment to the blog page and wait some time. After a small time, we can see the entries in the python server like this.
From that, we can get the cookie value of Sycamore. By loading the page with the cookie value we got from the server, the flag is revealed.
Web Penetration Testing 3 – Nonce-sense
After looking around the site while logged in as Sycamore, we notice that users can delete comments. The CSRF token prevents automated tools from testing payloads. Burp has a feature for this using macros.
We need to setup burp with a new session handling rule, record a macro and use it to generate new CSRF tokens for requests.
We need to add a custom parameter for CSRF tokens.
We need to ensure that what parameter we want to macro to update.
We need to define the scope of the session.
Then go to the Repeater and press the Go button. When you press the Go button, you can get the different CSRF tokens.
You can test some SQL injection here by adding ', after the comment_id=. So, we can notice that there is SQL injection vulnerability.
Get the request to a file and name it as “deletecomment_file”.
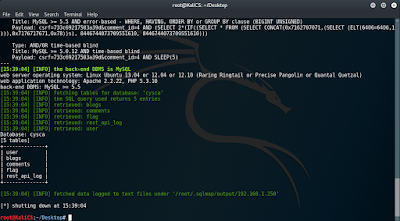
Now we have to do the rest using the sqlmap tool.
We can see the 5 tables in the cysca database. We use the “flag” table.
Finally, we can reveal the flag.































Nice post! This is a very nice blog that I will definitively come back to more times this year! Thanks for informative post.External Penetration Testing
ReplyDeleteIt’s really a great post with lots of blog commenting sites. It’s very important for getting traffic and really thanks for sharing all.
ReplyDeleteDigital Era
This hacker
ReplyDeleteblog sites was amazing and wonderful . its is such a very informative blog suite. I am glad to this informative and blog suits. Thanks for this information.
As an enigmatic digital realm, HACKERV!LLE thrives as a forum for tech aficionados. Its vibrant community shares insights on cybersecurity, hacking, and cutting-edge technologies. With a mix of tutorials and discussions, it's a dynamic space nurturing learning and collaboration, making it a haven for tech enthusiasts to explore and expand their knowledge.Digital Era
ReplyDeleteUsing social media platforms (e.g., Facebook, Instagram, Twitter, LinkedIn) to promote products or services, connect with the audience, and build brand awareness.social media marketing Social media marketing involves both organic (unpaid) and paid strategies.
ReplyDelete