Bandit Wargame
Hello, guys !!!
Today I'm bringing some interesting topic to you. That is Bandit(War game). Let's talk about the Active Directory.
Wargame is a concept where you can learn about some commands and train your self. your mind can improve your knowledge on hacking as well as to learn and practice your knowledge of Linux commands. Mainly these include the concepts of capture the flag logic behind it.You can also improve your password cracking skills, pen testing skills and much more other hacking techniques. I have provided a walkthrough on a game called Bandit. Here you can proceed from one level to another.
Login to http://overthewire.org/wargames/ Here you will be able to select the wargame you want to play.
Select Bandit. In this war game, there are 27 levels in which you have to complete one by one to proceed to the next level. Let's start with level zero.
I'm going to play
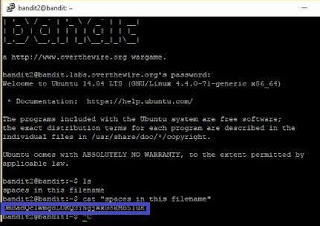
The password for the next level is stored in a file called "spaces in this filename". Use the cat command along with "" to get the password
Password for the next level is stored in the file name inhere directory. You need to go in to the directory and check the directory by using the command ls -al and get the password using the cat command .
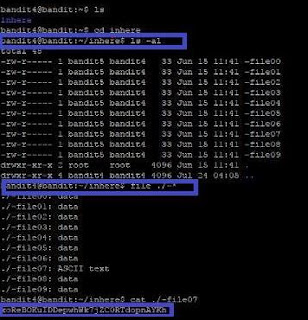
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
human-readable
1033 bytes in size
not executable
Use ls -l to view all the save items. Then use the find command with the required specifications.
The password for the next level is stored somewhere on the server and has all of the following properties:
owned by user bandit
owned by group bandit6
33 bytes in size
Use the find command with the above specifications
once you get the results use the cat command to grab the password
The password for the next level is stored in the file data.txt next to the word millionth
Next, use the below command to get the password
cat data.txt | grep millionth
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
use the ls command to view the data.txt file. Next, we need to find a unique line among many other details. For that use the below command and get the password.
cat data.txt | sort | unique -u
The password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ‘=’ characters.
for this use the ls command . Then use the below command to view the password.
string data.txt | grep '='
1: boJ9jbbUNNfktd78OOpsqOltutMc3MY1
2: CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
3: UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
4: pIwrPrtPN36QITSp3EQaw936yaFoFgAB
5: koReBOKuIDDepwhWk7jZC0RTdopnAYKh
6: DXjZPULLxYr17uwoI01bNLQbtFemEgo7
7: HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
8: cvX2JJa4CFALtqS87jk27qwqGhBM9plV
9: UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
10: truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
11: IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
12: 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
13: 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
14: 4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
15: BfMYroe26WYalil77FoDi9qh59eK5xNr
16: cluFn7wTiGryunymYOu4RcffSxQluehd
What is war game?
Wargame is a concept where you can learn about some commands and train your self. your mind can improve your knowledge on hacking as well as to learn and practice your knowledge of Linux commands. Mainly these include the concepts of capture the flag logic behind it.You can also improve your password cracking skills, pen testing skills and much more other hacking techniques. I have provided a walkthrough on a game called Bandit. Here you can proceed from one level to another.
Login to http://overthewire.org/wargames/ Here you will be able to select the wargame you want to play.
Select Bandit. In this war game, there are 27 levels in which you have to complete one by one to proceed to the next level. Let's start with level zero.
I'm going to play
Level 0
The goal of this level is for you to log into the game using SSH.Download Putty, we use putty as an SSH client on windows. Once done to connect to the host use the below details and log in with the given credentials.
Host name : bandit.labs.overthewire.org
Port : 2220
Level 0 - 1
After login in use the ls command to view all the directories.
Now you will find a readme file. You can read this by using the cat command.
Level 1 - 2
Login to level 1 using the above details.Now use again the ls command to find the - file and again use the cat command and get the password.
Level 2 - 3
The password for the next level is stored in a file called "spaces in this filename". Use the cat command along with "" to get the password
Level 3 - 4
Password for the next level is stored in the file name inhere directory. You need to go in to the directory and check the directory by using the command ls -al and get the password using the cat command .
Level 4 - 5
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
Level 5 - 6
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
human-readable
1033 bytes in size
not executable
Use ls -l to view all the save items. Then use the find command with the required specifications.
Level 6 - 7
The password for the next level is stored somewhere on the server and has all of the following properties:
owned by user bandit
owned by group bandit6
33 bytes in size
Use the find command with the above specifications
once you get the results use the cat command to grab the password
Level 7 - 8
The password for the next level is stored in the file data.txt next to the word millionth
Next, use the below command to get the password
cat data.txt | grep millionth
Level 8 - 9
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
use the ls command to view the data.txt file. Next, we need to find a unique line among many other details. For that use the below command and get the password.
cat data.txt | sort | unique -u
Level 9 - 10
The password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ‘=’ characters.
for this use the ls command . Then use the below command to view the password.
string data.txt | grep '='
1: boJ9jbbUNNfktd78OOpsqOltutMc3MY1
2: CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
3: UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
4: pIwrPrtPN36QITSp3EQaw936yaFoFgAB
5: koReBOKuIDDepwhWk7jZC0RTdopnAYKh
6: DXjZPULLxYr17uwoI01bNLQbtFemEgo7
7: HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
8: cvX2JJa4CFALtqS87jk27qwqGhBM9plV
9: UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
10: truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
11: IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
12: 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
13: 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
14: 4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
15: BfMYroe26WYalil77FoDi9qh59eK5xNr
16: cluFn7wTiGryunymYOu4RcffSxQluehd














Comments
Post a Comment